Skip to main content
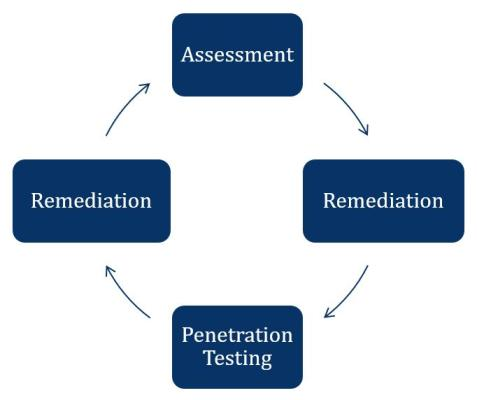
Assessment
- Assessment of information security program, environmental factors, and technical area review
- Purpose is to identify potential gaps in coverage as well as provide baseline of improvement recommendations
- Conducted using industry best practices and DOD Security Technical Implementation Guidelines (STIGs)
- Output is comprehensive report outlining vulnerabilities and recommended solutions
Remediation
- Utilize assessment report to prioritize and address vulnerabilities
- Determine acceptable risk levels and document risk mitigation strategy
- Develop internal processes, policies and procedures to improve security posture
- Leverage report to determine additional resource requirements
Penetration Testing
- Validate the steps taken during remediation to ensure appropriate resolution
- Identify additional areas of concern including user awareness and network monitoring capability
- Output is comprehensive report detailing actions taken and recommended solutions
Remediation
- Address vulnerabilities outlined in penetration testing report
- Identify additional risk acceptance and document mitigation strategy
- Evaluate processes, policies, and procedures to ensure comprehensive coverage
- Leverage report to determine additional resource requirements
Contact
nc.csrf@army.mil